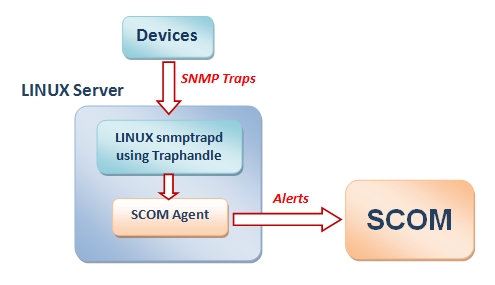
This Linux machine is in turn monitored by SCOM, via the SCOM agent for Linux.
We will use this agent to generate the alerts from SNMP traps:
Steps:
1- Preparing the LINUX system
:
Ensure that the NET-SNMP package is installed.
Edit the file /etc/snmp/snmptrapd.conf, bellow is my default conf: the received traps are always logged to /var/log/snmptrapd.log
disableAuthorization yes
authCommunity log public
logoption f /var/log/snmptrapd.log
logoption s 2
2- Create a management pack that reads alerts from files and inserts them into SCOM
This MP can check, for instance, ~monuser/alerts/new and if there are any files then it inserts them into SCOM, as alerts. The data inside these files must follow a predefined format, such as:
Alert Severity | Alert Priority | Alert name | Alert description | <Other fields you need> ...Once a file is processed it is removed or moved to other directory.
3- Insert the MIB file into the LINUX system
This is made by placing the mib file into a certain path, normally /usr/local/share/snmp/mibs
Then edit /etc/snmp/snmpd.conf and add the following line:
# Read mib file
mibfile /usr/share/snmp/mibs/<your mib file>
4- Develop a shell script, for instance named trap2scom.sh, for receiving trap data and creating alert files
It should be something like:
#!/bin/bash
read host
read ip
vars=
while read oid val
do
val=$(echo $val | tr -dc '[:print:]')
val=${val//\|/\:}
oid=$(echo $oid | tr -dc '[:print:]')
oid=${oid//\|/\:}
vars="$vars$oid = $val
"
oid=${oid//\./\_}
oid=${oid//\:/\_}
oid=${oid// /\_}
oid=$(echo ${oid// /\_} | tr -dc '[:alnum:]_')
eval "Var_$oid=$val"
done
# Create alert file with the following fields:
# owner | origin (device) | severity | priority | name | description |!|
FOUT="alert${RANDOM}.alr"
cd ~monuser/alerts/new
echo "SNMP_Trap | $host | 0 | 1 | $1 | $vars" '|!|' > $FOUT
chown monuser $FOUT
Note: This is the default behavior but this script also sets the trap's bind variables as script variables (named Var_<bind variable>) so you can use them to check certain values before creating the alert. Also the severity might depend on a certain variable. For instance:
if [ "$Var_Severity" -eq "critical" ]
then
# Create a critical alert ....
fi
5- Edit again the file /etc/snmp/snmptrapd.conf and add handles for the traps you want to process
traphandle <your-mib>::<trap-name> <path-to-your-script>/trap2scom.sh MyAlert
Finally restart the daemon snmptrapd. In RedHat the command is:
service snmptrapd restart